I recently needed to create a new site to site VPN, but there was a few challenges to this. First of all the router of the new site is behind NAT and it would be moved to other physical locations everynow and then. I needed something that works both behind NAT and initiates the connection, that’s when I started to think about wireguard. I have used wireguard in the past, so it wasn’t exactly new to me.
The other challenge was overlapping networks. The new site used 192.168.1.0/24 for it’s network and I already had that network connected to my site. So I need to use Network Address Translation to rewrite the source/destination address of the packages.
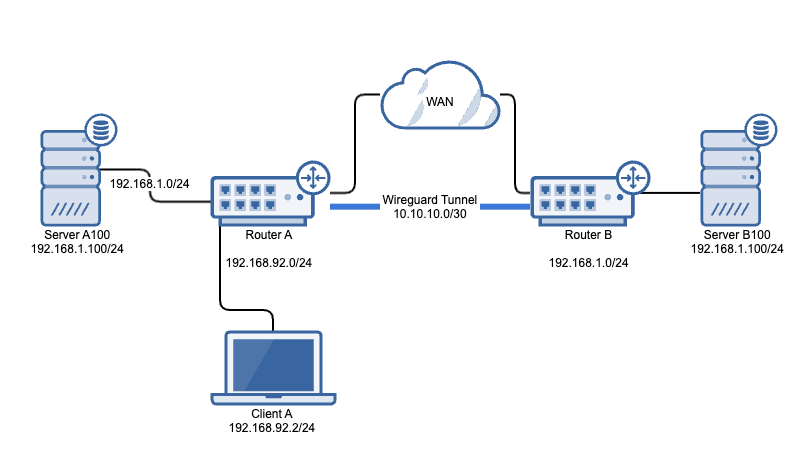
Site A
LAN Network 1: 192.168.92.0/24
LAN Network 2: 192.168.1.0/24
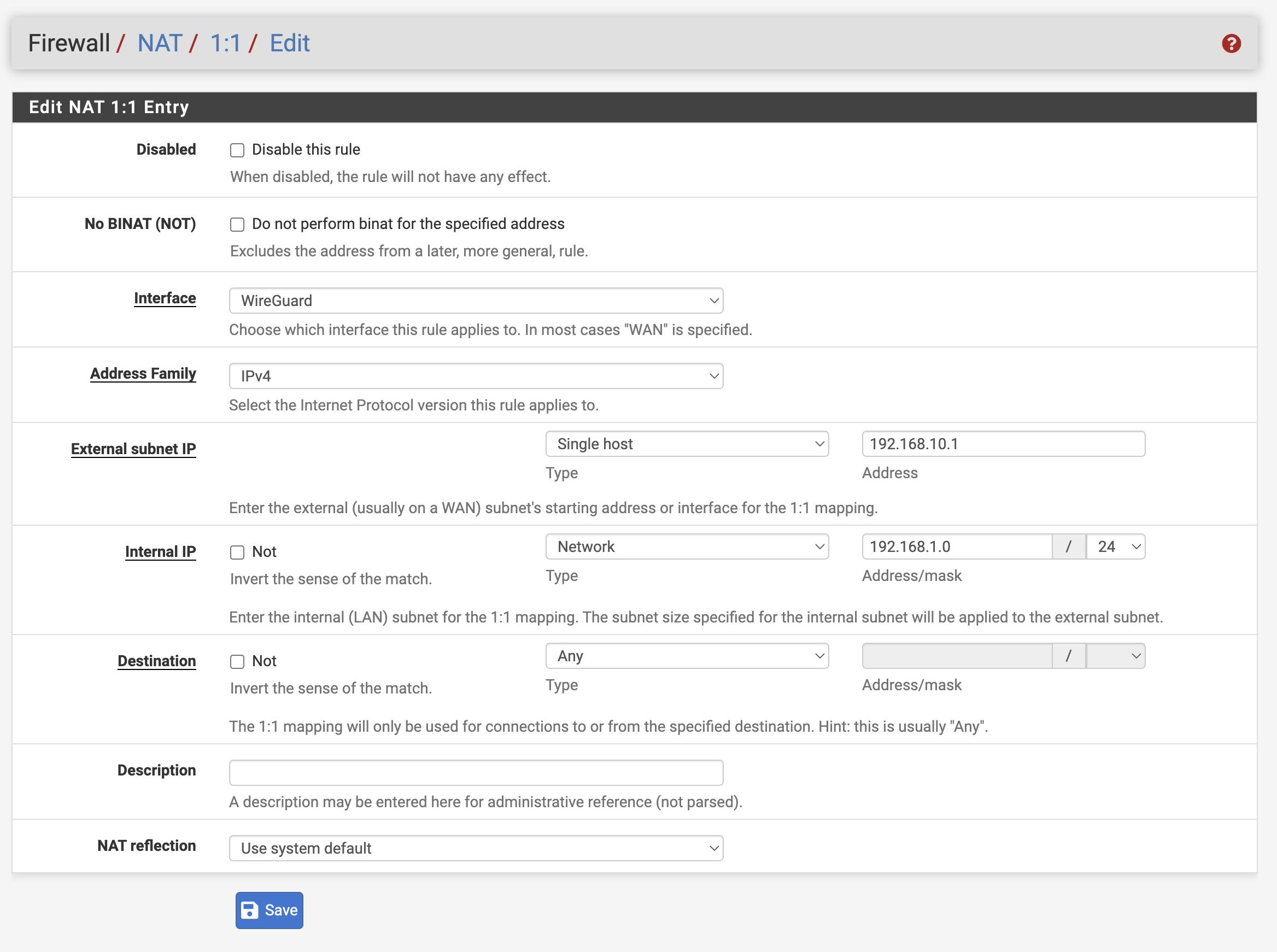
Translated network for Site B: 192.168.10.0/24
Wireguard Interface: 10.10.10.1/30
Site B
LAN Network: 192.168.1.0/24
Wireguard Interface: 10.10.10.2/30
Here’s how it works. Without NAT a packet from Client A (192.168.92.2) to 192.168.1.100 would arrive at Server A100 (192.168.1.100) since network 192.168.1.0/24 is physically connected to Router A, so how do we get the traffic to Server B100?
This is where 1:1 NAT comes in.
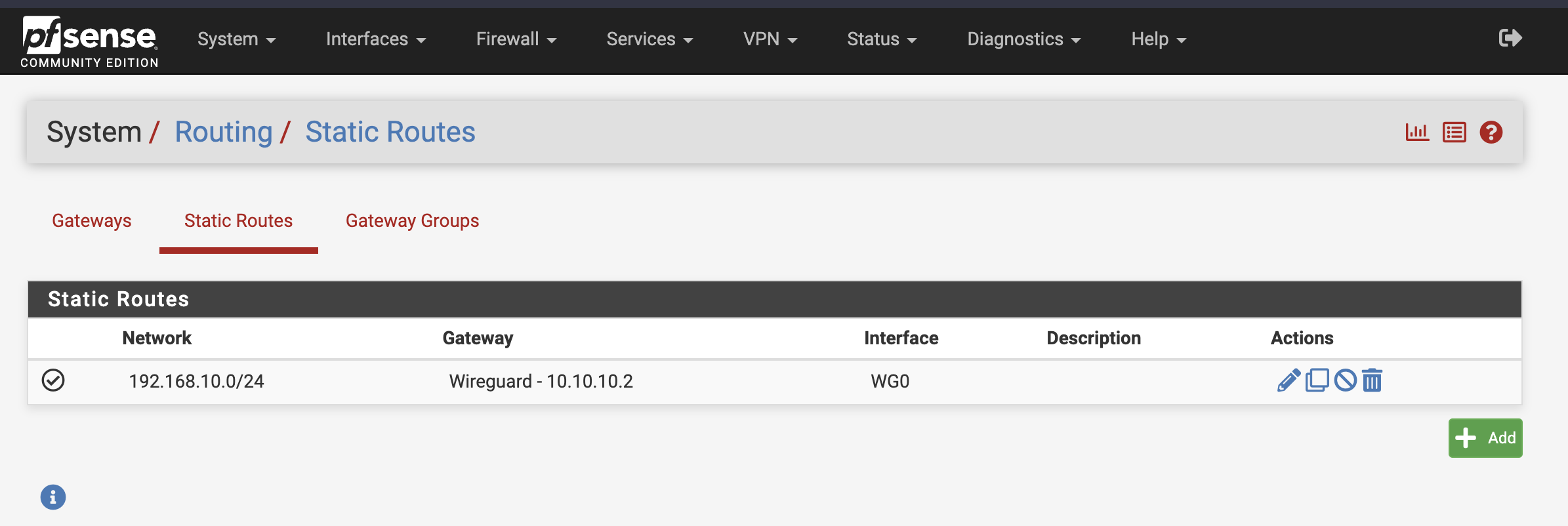
- On Router A, create a static route for network 192.168.10.0/24 destined to an interface on Router B (Wireguard 10.10.10.2/30 in my case).
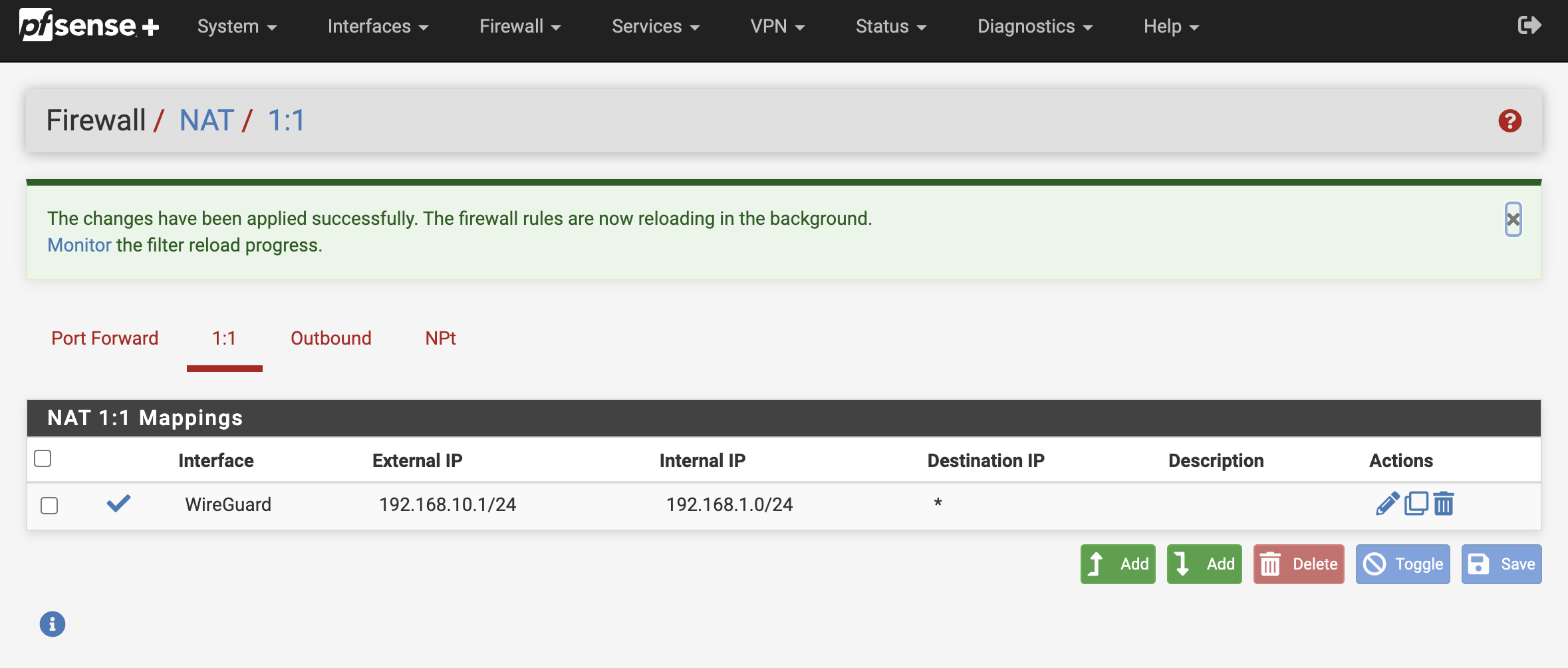
- On Router B NAT rules are created so packages destined to network 192.168.10.0/24 gets rewritten to 192.168.1.0/24 which is physically connected at Router B. This means whenever Client A needs to communicate with Server B100, it needs to use IP 192.168.10.100 instead. Read more about NAT here
| Source Address | Destination Address | Rewritten Destination Address |
|---|---|---|
| 192.168.92.2 | 192.168.10.100 | 192.168.1.100 |
I won’t go into details about how Wireguard works or is set up, so if you need help with that, look at the documentation HERE
Configuration Site A
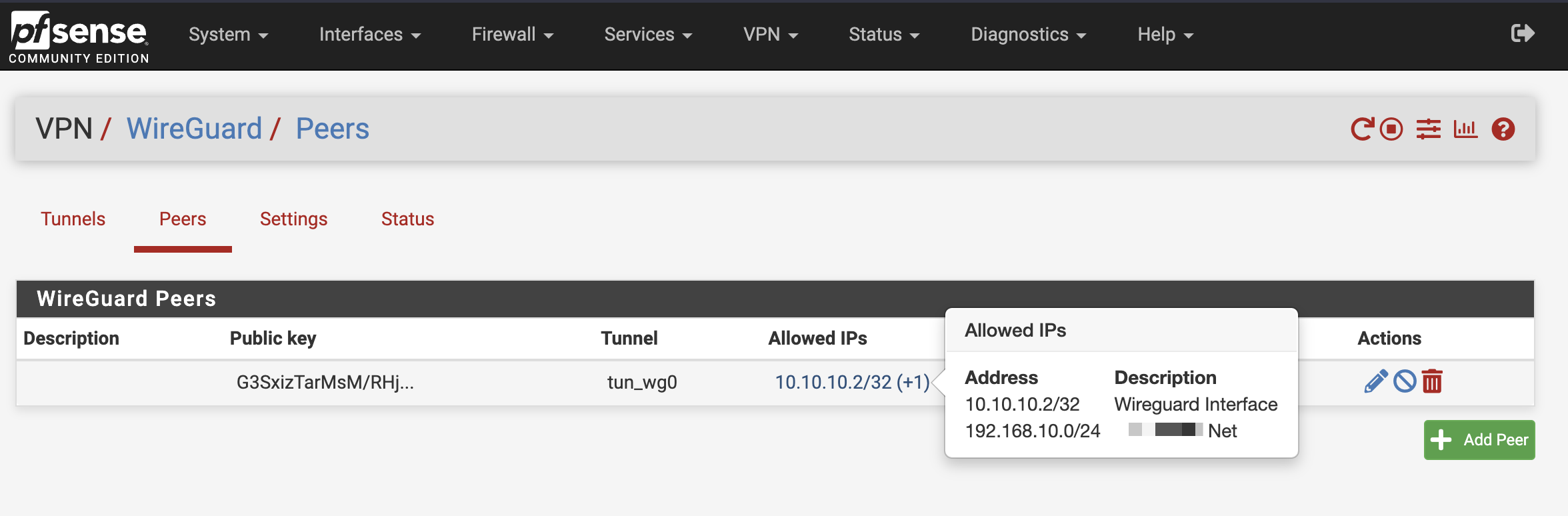
Allow access to the opposite network in wireguard. Please note that I’m using 192.168.10.0/24 as my translated network for site B
1. Wireguard interface assignment and settings
2. Firewall Rules
Create a firewall rule that allows all traffic over the wireguard tunnel. You can always make it more strict later on, when you know it’s working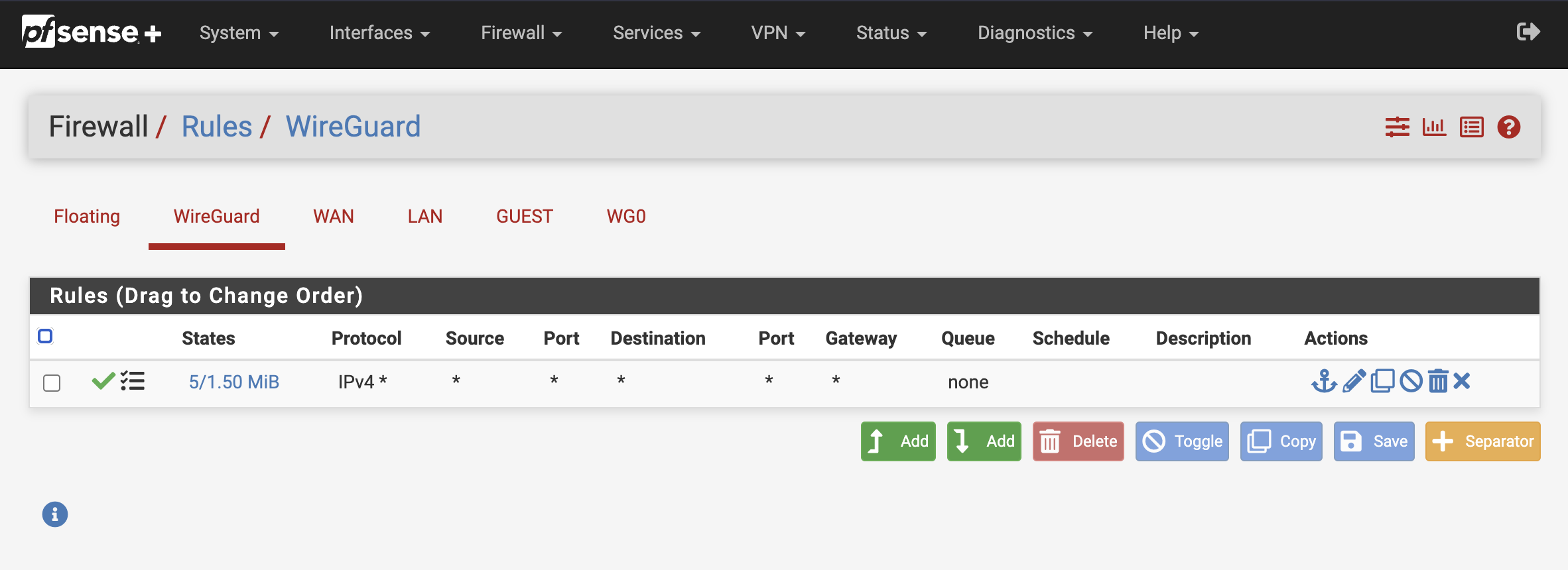
3. Create a static route to Site B
Configuration Site B
Allow access to the opposite network in wireguard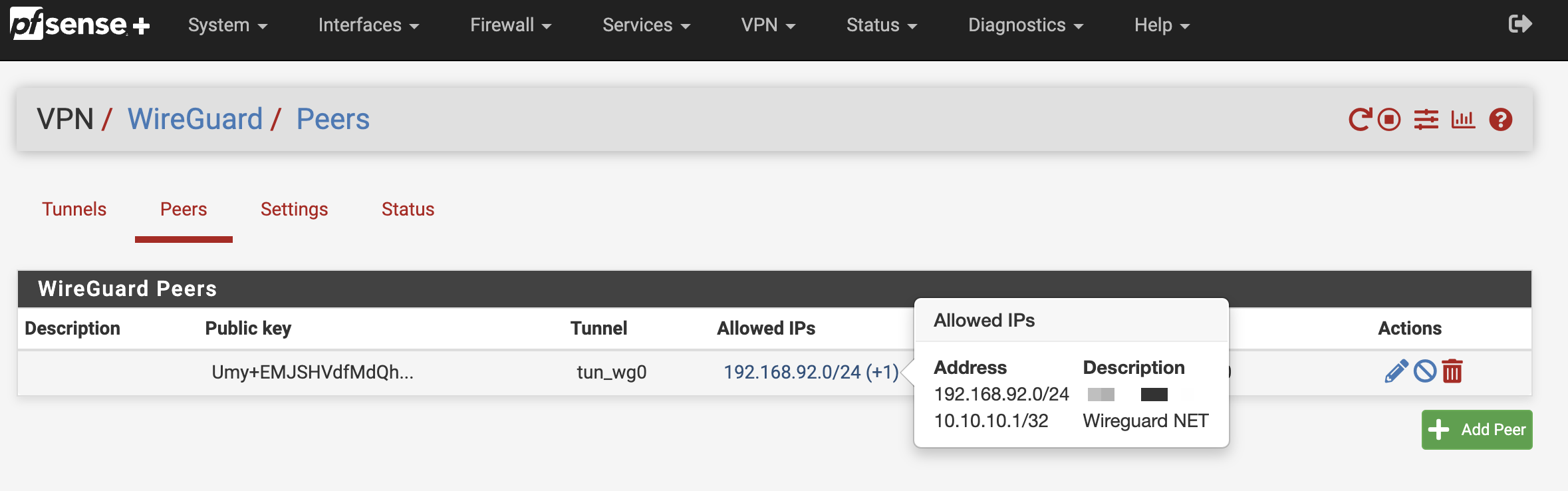
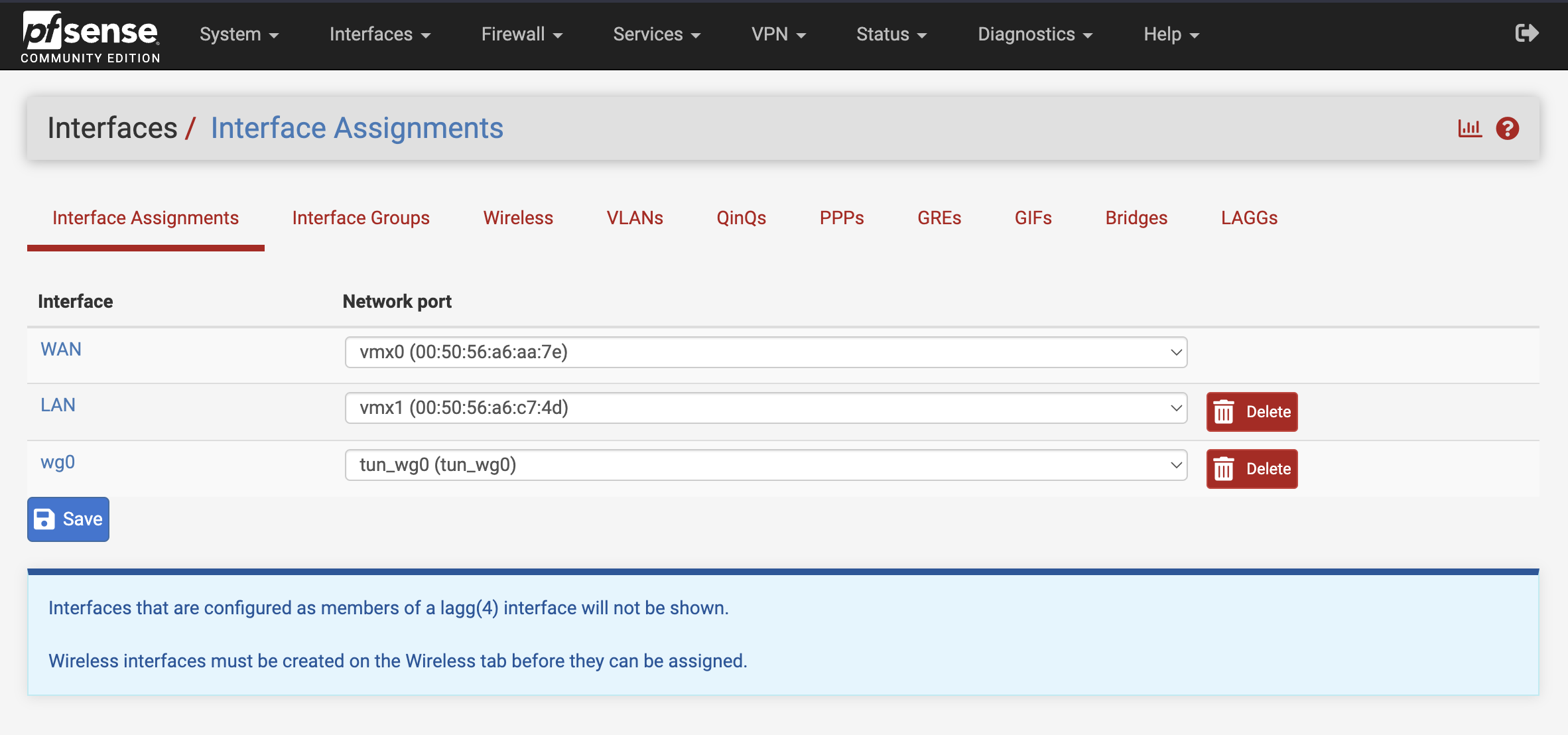
1. Assign wireguard to a interface
Find your wireguard network port in the dropdown list and add it as an interface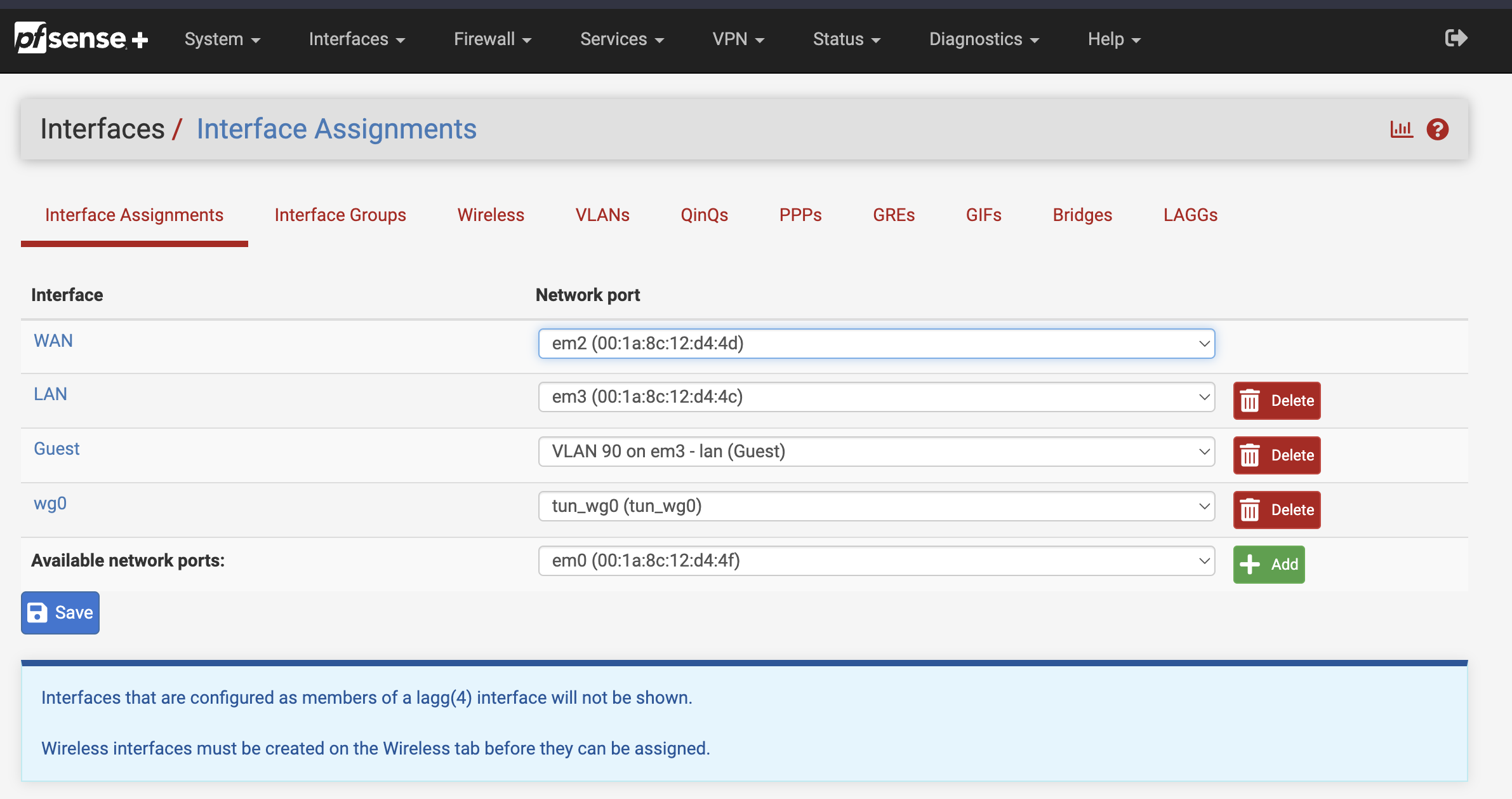
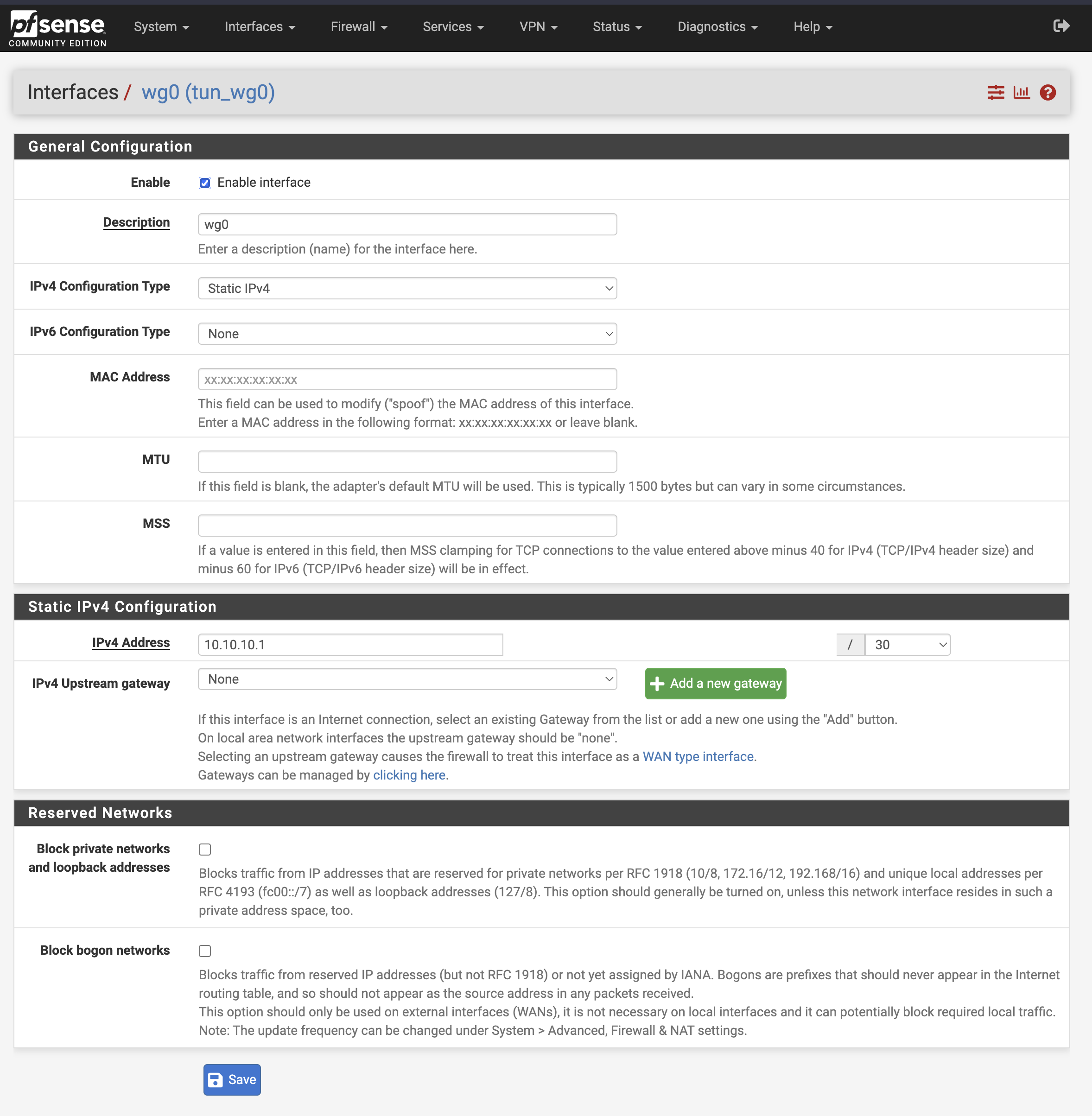
Give the interface a static IPv4 addres. I’m using 10.10.10.2/30 on Site B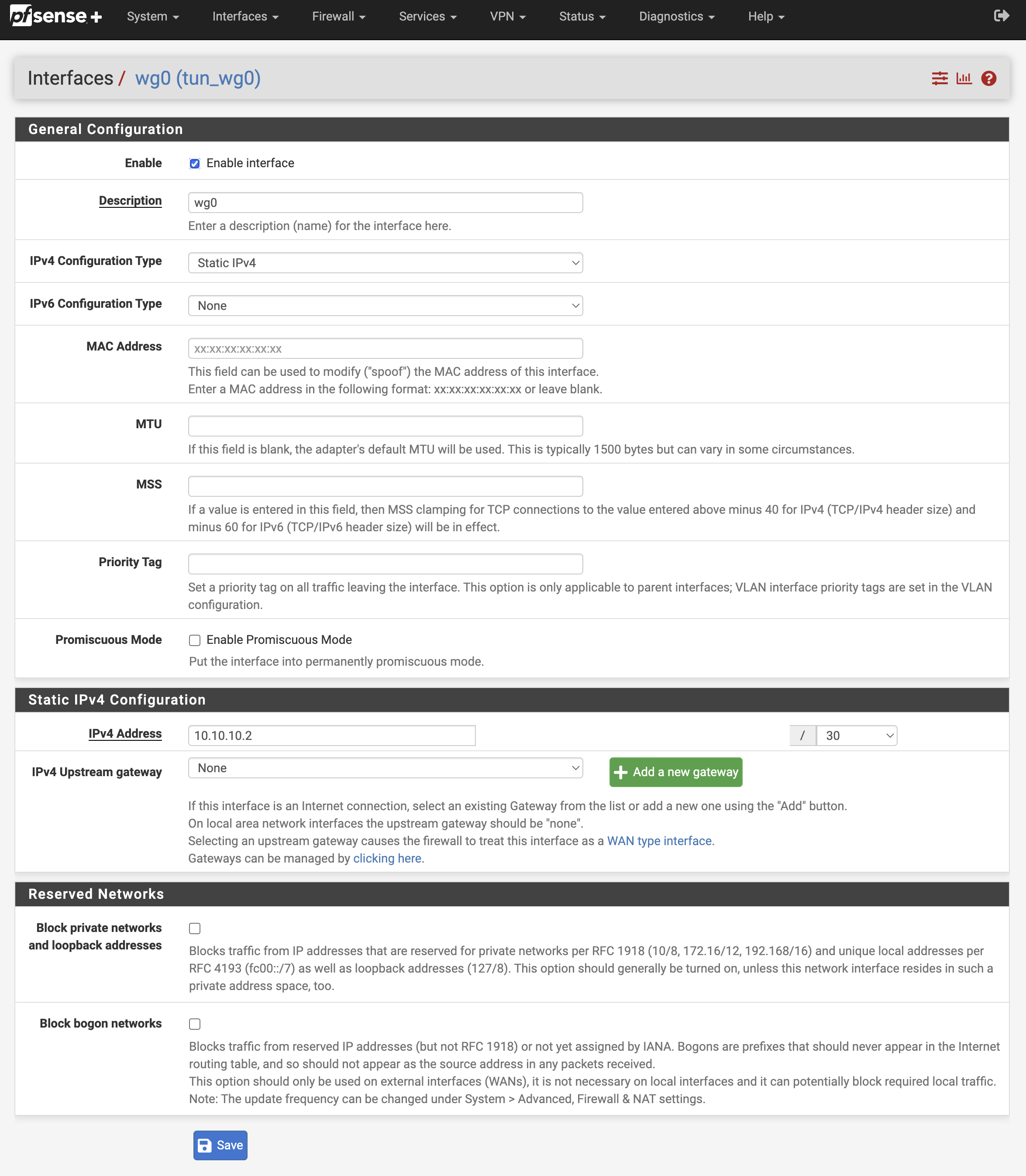
2. Firewall Rules
Create a firewall rule that allows all traffic over the wireguard tunnel
3. Outbound NAT
Traffic destined to 192.168.92.0/24 needs it’s source to be rewritten to an address in the 192.168.10.0/24 network. I’m using Bitmask to keep the last portion of the address identical during translation, it makes it a lot easier when looking at firewall logs.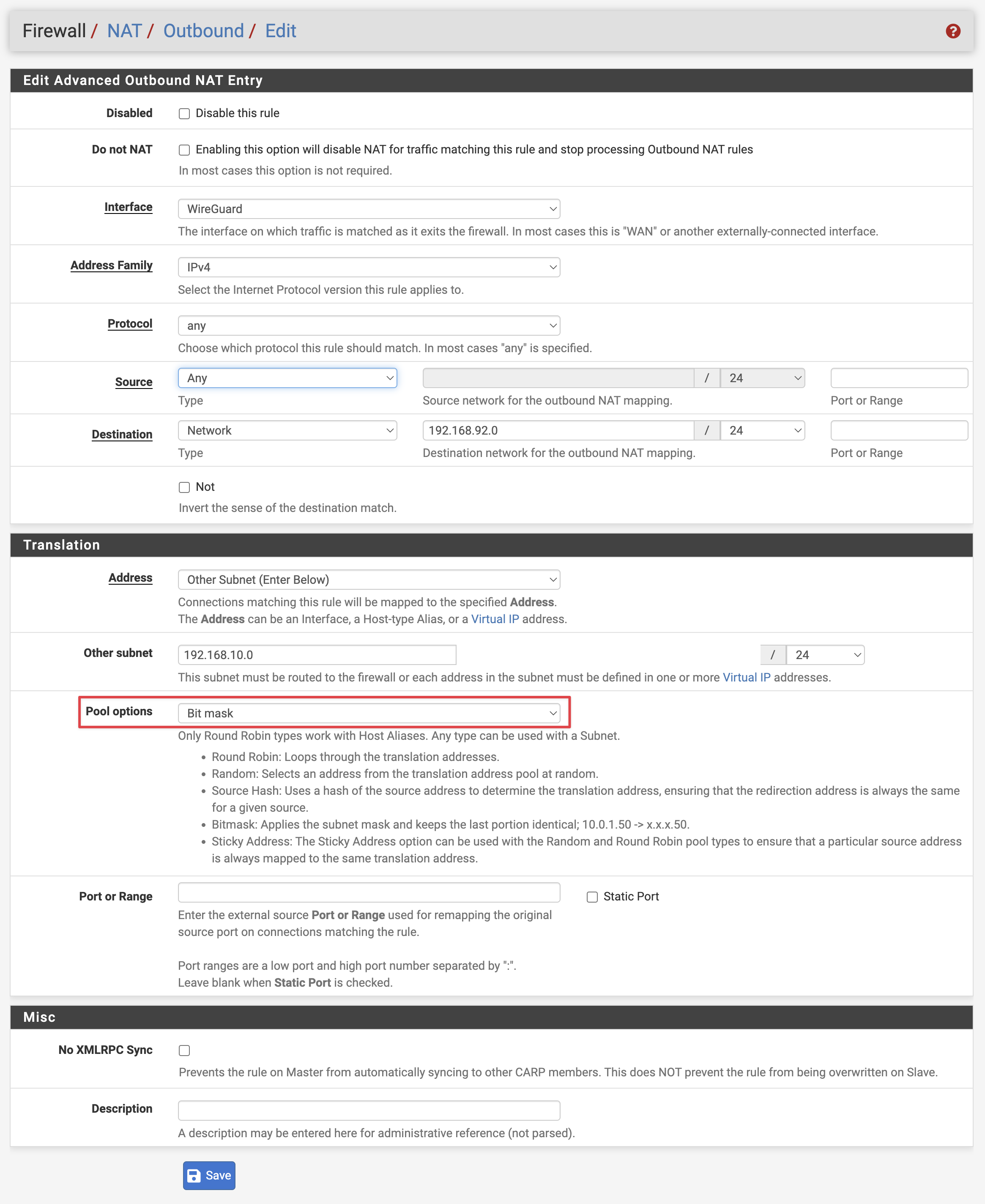
Set Outbound NAT Mode to Hybrid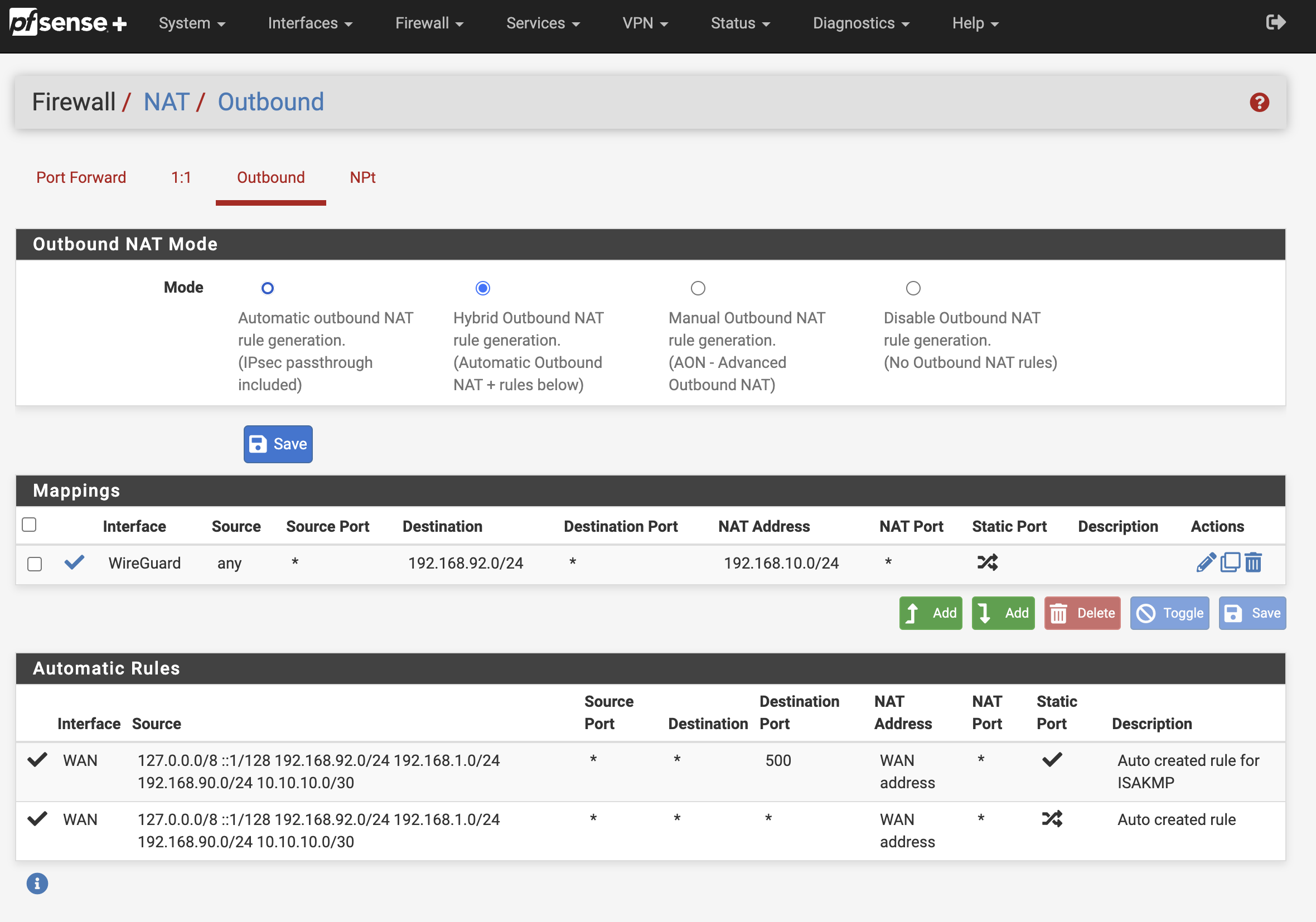
3.1. Create a 1:1 NAT rule
Create a rule, so traffic incoming traffic on the wireguard interface to network 192.168.10.0/24 is translated to 192.168.1.0/24